Port Scanning: It's Not Just an Offensive Tool Anymore
Gary C. Kessler
May 2001
Port Scanning: It's Not Just an ..
<blockquote>An edited version of this paper with the title "Plugging Leaky Holes" originally appeared in the June 2001 issue of Information Security Magazine (www.infosecuritymag.com). Copyright © 2001. All rights reserved.
</blockquote>
Systemadministrators are constantly being advised to check their systems foropen ports and services that might be running that are eitherunintended or unnecessary. In some cases, the services might be Trojansjust waiting to be exploited.
The most common host-based tool for checking for open ports on Windows or Unix systems is the netstatcommand. But running this command means actually walking or remotelyaccessing each and every server; and you miss other host systems thatmight be listening on improper ports. This is where ports canners comein; with this tool, a system, network, or security administrator cancheck a group of hosts all at once.
Port scanningsoftware has long been in the hacker's arsenal and is finally emergingas an important defensive tool as well. Originally only available forUnix/Linux systems and distributed on underground hacker web sites,port scanners are now also available for Windows platforms and haveeven entered the realm of reputable, commercial software. If you don'tknow what a port scanner is, you should; and if you don't use a portscanner to test your defenses, you should.
So, What's a Port?
Let'sstart with the basics. In the TCP/IP protocol stack, messagesassociated with the common application protocols that most of us arefamiliar with — such as HTTP for the Web; SMTP, POP, and IMAP fore-mail; Telnet and SSH for remote logon; and FTP for file transfers —operate over the Transmission Control Protocol (TCP) or User DatagramProtocol (UDP); TCP and UDP messages, in turn, are carried insideInternet Protocol (IP) packets. The primary difference between TCP andUDP is that TCP is connection-oriented and UDP is connectionless. Whenusing TCP, then, two hosts must first establish a logical connectionbefore they can exchange data (analogous to establishing a telephoneconnection) while hosts using UDP do not require a logical connectionbefore the exchange of information (analogous to sending a letterthrough the postal service).
Both TCP and UDP employ port numbersto identify the higher layer applications at the hosts that arecommunicating with each other. End-to-end data communications on theInternet, in fact, are uniquely identified by the source anddestination host IP addresses and the source and destination TCP/UDPport numbers.
TCP/IP applications generally employ aclient/server model, exemplified by the relationship between your Webclient software (i.e., the browser) and a Web server; the user "points"their browser at the Web server which is usually listening on port 80.Port numbers can take on a value between 1 and 65535, with serverapplications generally being assigned a value below 1024. There are alarge number of so-called well-known ports, including:
A complete list of port numbers can be found at the Internet Assigned Numbers Authority (IANA) list of port numbers at http://www.iana.org/assignments/port-numbers.[/size]Port Scanner Operation
[size=12]A port scanner,most simply, probes a computer system running TCP/IP to determine whichTCP and UDP ports are open and listening, which indicates all of theservices that this system is offering to other TCP/IP hosts. As anexample, you would expect an e-mail server to be listening on the SMTPand POP3 ports, and a Web server to be listening on the HTTP, andperhaps the SSL/HTTPS, ports. For good or for bad, however, mostsystems have many more open ports than intended. You can use the netstat -a command to find out which ports are open on a local Linux/Unix or Windows system (Figure 1), but netstat can't be used remotely across a network.
Whilefirewalls presumably block inappropriate traffic going in and out of agiven Internet site, they can't protect a server from intended traffic;incoming HTTP traffic to the Web server, for example, is appropriate and will not be blocked. Those servers have to be secured and protected themselves.Oncean attacker has found available servers using a port scanner, he or shecan use this information to attempt to connect to those services,determine what specific software is running, and check to see if thereare any known vulnerabilities with that software that might beexploited. Port scanners are particularly effective when they findunadvertised servers since many sites fail to adequately protect theseexperimental, non-production systems since "no one knows about them."As an example, attackers can use port scanners to look for systemsrunning Web or DNS services. They can then target those hosts lookingfor vulnerable software, such as older versions of the InternetInformation Service (IIS) or exploitable versions of the BerkeleyInternet Domain Daemon (BIND).Portscanners can also be used to examine hosts for known Trojan horses,distributed denial-of-service (DDoS) tools, or other malicious servicesrunning on a host. These kinds of port scans or port probes are seenall of the time. A short list of some of the default "bad" ports are:
Forusers who prefer a graphical user interface (GUI), there is also agraphical front end for nmap (Figure 3). The nmap GUI shows a number ofinteresting features such as how to easily change the form of the portscanning attack. The most basic form of port scanning might beaccomplished by attempting to establish a Telnet session to each porton the target host in sequence; successful connections indicate an openport. But not only is this type of attack time consuming, it is sure tobe detected if the target network uses any form of logging or intrusiondetection.Severalforms of "quiet" port scanning can be used, however, that are lessdetectable. In one scheme, the attacker starts to establish a Telnetconnection on each port on the target host but does not complete therequired three-way SYN/ACK handshake. Another method is for theattacker to close a non-existent Telnet connection on ports on thetarget host; by monitoring the target host's response, the attacker candetermine whether the port was open in the first place. There are othermethods as well, and one of the best descriptions of port scanning canbe found in "The Art of Port Scanning" by Fyodor (nmap's author) in Phrack Magazine (http://www.phrack.com/search.phtml?view&article=p51-11). Both the command line and GUI for nmap support many types of port scanning probes.Securitymanagers are constantly told that a site needs to have a securitypolicy. Once policies have been written, they need to be implementedand this includes configuring the firewall to properly allow and denytraffic. nmap can play an important role in auditing the firewall, orensuring that the firewall actually implements the intended policies,by testing to see what ports are allowed to pass through the firewall.In this way, the defender — or attacker — can learn which ports thefirewall is defending and which applications are only protected by theserver itself.(Testingthe ports that can pass through the firewall is very different thantesting what ports — or services — are open at the firewall.Determining what ports are open at the firewall yields possible ways to attack the firewall itself. Testing to see what ports are allowed to pass throughthe firewall allows the sysadmin to ensure that the firewall packetfiltering is performing as desired and properly protecting the internalsystems.)Another important tool in this genre is hping, which might be best described as a port scanner on steroids (http://www.kyuzz.org/antirez/hping.html).hping is a Unix-based command-line TCP/IP packet assembler/analyzer. Itcan be used for many tasks, including firewall testing, advanced portscanning, network and intrusion detection testing (by crafting TCP/IPpackets), remote OS fingerprinting, and TCP/IP stack auditing.Other Port Scanning SoftwarePortscanning software is no longer limited to the Linux/Unix environment.nmap itself has now been ported (no pun intended!) to Windows NT andcan be found at eEye Digital Security's Web site at http://www.eeye.com/html/Research/Tools/nmapnt.html.
There are other Windows-based port scanners and one of the better ones can be found at the J. River Network Toolbox Web site (http://www.jriver.com).As shown in Figure 4, this port scanner finds open TCP, but not UDP,ports. The software also includes ping, traceroute, IP addressscanning, finger, and whois functions.
Foundstone, the company founded by the three authors of the most excellent book Hacking Exposed, distributes SuperScan (Figure 5), a port scanner that is among several interesting tools available at their site (http://www.foundstone.com).WildPackets distributes iNetTools, an add-on to their EtherPeek packetsniffer software, that includes DNS lookup, finger, name lookup andscanning, ping, port scanning, traceroute, and whois (http://www.wildpackets.com/products/inettools).CONCLUSIONWhyuse a "hacker tool" to help defend your network? There are a number ofreasons. First, the hackers use this tool because it is a good way tolearn about your network. You can use it to learn about your network,too. You can also learn what the hackers are learning about yournetwork. Second, port scanning provides an excellent way in which youcan audit your network's security policies and as a first pass towardsassessing your network's potential exposures.Bottom-line:A port scanner is an important tool in the security manager's toolkit.It has, like all of the best security tools today, both offensive anddefensive capabilities — but that is no reason not to use it yourself.
ABOUT THE AUTHOR:Gary C. Kessler is an Assistant Professor and program coordinator ofthe Computer Networking major at Champlain College in Burlington,Vermont, and an independent consultant and writer. His e-mail addressis kumquat@sover.net
Gary C. Kessler
May 2001
Port Scanning: It's Not Just an ..
<blockquote>An edited version of this paper with the title "Plugging Leaky Holes" originally appeared in the June 2001 issue of Information Security Magazine (www.infosecuritymag.com). Copyright © 2001. All rights reserved.
</blockquote>
Systemadministrators are constantly being advised to check their systems foropen ports and services that might be running that are eitherunintended or unnecessary. In some cases, the services might be Trojansjust waiting to be exploited.
The most common host-based tool for checking for open ports on Windows or Unix systems is the netstatcommand. But running this command means actually walking or remotelyaccessing each and every server; and you miss other host systems thatmight be listening on improper ports. This is where ports canners comein; with this tool, a system, network, or security administrator cancheck a group of hosts all at once.
Port scanningsoftware has long been in the hacker's arsenal and is finally emergingas an important defensive tool as well. Originally only available forUnix/Linux systems and distributed on underground hacker web sites,port scanners are now also available for Windows platforms and haveeven entered the realm of reputable, commercial software. If you don'tknow what a port scanner is, you should; and if you don't use a portscanner to test your defenses, you should.
So, What's a Port?
Let'sstart with the basics. In the TCP/IP protocol stack, messagesassociated with the common application protocols that most of us arefamiliar with — such as HTTP for the Web; SMTP, POP, and IMAP fore-mail; Telnet and SSH for remote logon; and FTP for file transfers —operate over the Transmission Control Protocol (TCP) or User DatagramProtocol (UDP); TCP and UDP messages, in turn, are carried insideInternet Protocol (IP) packets. The primary difference between TCP andUDP is that TCP is connection-oriented and UDP is connectionless. Whenusing TCP, then, two hosts must first establish a logical connectionbefore they can exchange data (analogous to establishing a telephoneconnection) while hosts using UDP do not require a logical connectionbefore the exchange of information (analogous to sending a letterthrough the postal service).
Both TCP and UDP employ port numbersto identify the higher layer applications at the hosts that arecommunicating with each other. End-to-end data communications on theInternet, in fact, are uniquely identified by the source anddestination host IP addresses and the source and destination TCP/UDPport numbers.
TCP/IP applications generally employ aclient/server model, exemplified by the relationship between your Webclient software (i.e., the browser) and a Web server; the user "points"their browser at the Web server which is usually listening on port 80.Port numbers can take on a value between 1 and 65535, with serverapplications generally being assigned a value below 1024. There are alarge number of so-called well-known ports, including:
- TCP 20 and 21 (File Transfer Protocol, FTP)
- TCP 22 (Secure Shell, SSH)
- TCP 23 (Telnet)
- TCP 25 (Simple Mail Transfer Protocol, SMTP)
- TCP and UDP 53 (Domain Name System, DNS)
- UDP 69 (Trivial File Transfer Protocol, tftp)
- TCP 79 (finger)
- TCP 80 (Hypertext Transfer Protocol, HTTP)
- TCP 110 (Post Office Protocol v3, POP3)
- TCP 119 (Network News Protocol, NNTP)
- UDP 161 and 162 (Simple Network Management Protocol, SNMP)
- UDP 443 (Secure Sockets Layer over HTTP, https)
A complete list of port numbers can be found at the Internet Assigned Numbers Authority (IANA) list of port numbers at http://www.iana.org/assignments/port-numbers.[/size]Port Scanner Operation
[size=12]A port scanner,most simply, probes a computer system running TCP/IP to determine whichTCP and UDP ports are open and listening, which indicates all of theservices that this system is offering to other TCP/IP hosts. As anexample, you would expect an e-mail server to be listening on the SMTPand POP3 ports, and a Web server to be listening on the HTTP, andperhaps the SSL/HTTPS, ports. For good or for bad, however, mostsystems have many more open ports than intended. You can use the netstat -a command to find out which ports are open on a local Linux/Unix or Windows system (Figure 1), but netstat can't be used remotely across a network.
. FIGURE 1: The netstat command can be used from the Linux or Windows command line to check on open ports on the local computer. |
Whilefirewalls presumably block inappropriate traffic going in and out of agiven Internet site, they can't protect a server from intended traffic;incoming HTTP traffic to the Web server, for example, is appropriate and will not be blocked. Those servers have to be secured and protected themselves.Oncean attacker has found available servers using a port scanner, he or shecan use this information to attempt to connect to those services,determine what specific software is running, and check to see if thereare any known vulnerabilities with that software that might beexploited. Port scanners are particularly effective when they findunadvertised servers since many sites fail to adequately protect theseexperimental, non-production systems since "no one knows about them."As an example, attackers can use port scanners to look for systemsrunning Web or DNS services. They can then target those hosts lookingfor vulnerable software, such as older versions of the InternetInformation Service (IIS) or exploitable versions of the BerkeleyInternet Domain Daemon (BIND).Portscanners can also be used to examine hosts for known Trojan horses,distributed denial-of-service (DDoS) tools, or other malicious servicesrunning on a host. These kinds of port scans or port probes are seenall of the time. A short list of some of the default "bad" ports are:
- 1243/tcp: SubSeven server (default for V1.0-2.0)
- 6346/tcp: Gnutella
- 6667/tcp: Trinity intruder-to-master and master-to-daemon
- 6667/tcp: SubSeven server (default for V2.1 Icqfix and beyond)
- 12345/tcp: NetBus 1.x
- 12346/tcp: NetBus 1.x
- 16660/tcp: Stacheldraht intruder-to-master
- 18753/udp: Shaft master-to-daemon
- 20034/tcp: NetBus Pro
- 20432/tcp: Shaft intruder-to-master
- 20433/udp: Shaft daemon-to-master
- 27374/tcp: SubSeven server (default for V2.1-Defcon)
- 27444/udp: Trinoo master-to-daemon
- 27665/tcp: Trinoo intruder-to-master
- 31335/udp: Trinoo daemon-to-master
- 31337/tcp: Back Orifice
- 33270/tcp: Trinity master-to-daemon
- 33567/tcp: Backdoor rootshell via inetd (from Lion worm)
- 33568/tcp: Trojaned version of SSH (from Lion worm)
- 40421/tcp: Masters Paradise Trojan horse
- 60008/tcp: Backdoor rootshell via inetd (from Lion worm)
- 65000/tcp: Stacheldraht master-to-daemon
. FIGURE 2: nmap command line tools for Linux/Unix. |
.  FIGURE 3: nmap graphical front end for Linux/Unix. |
تكبير الصورةتصغير الصورة تم تعديل ابعاد هذه الصورة. انقر هنا لمعاينتها بأبعادها الأصلية. 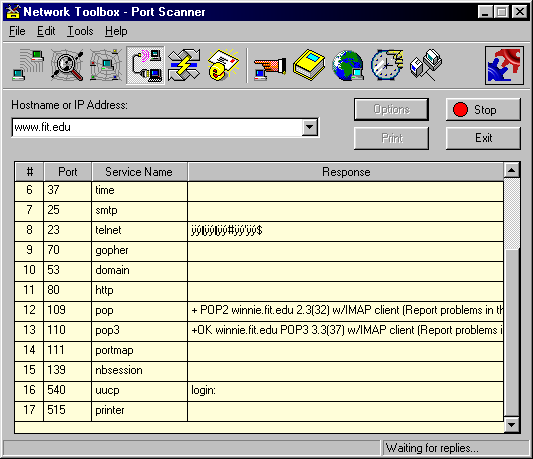 FIGURE 4: Port scanner function in the J. River Network Toolbox. |
تكبير الصورةتصغير الصورة تم تعديل ابعاد هذه الصورة. انقر هنا لمعاينتها بأبعادها الأصلية.  FIGURE 5: Foundstone's SuperScan port scanner. |
ABOUT THE AUTHOR:Gary C. Kessler is an Assistant Professor and program coordinator ofthe Computer Networking major at Champlain College in Burlington,Vermont, and an independent consultant and writer. His e-mail addressis kumquat@sover.net

